Authenticating Git clients to TFS using Kerberos
You can authenticate to correctly configured instances of Visual Studio Team Foundation Server by using Kerberos over the Negotiate (SPNEGO) protocol. By using authentication with a Kerberos ticket, you can more securely authenticate from supported clients to your server without providing your password. After you obtain a Kerberos ticket, you can configure your git client to use Kerberos.
Team Foundation Server accepts only NTLM credentials by default, however it may be configured to accept Kerberos authentication. Access the Team Foundation Server Configuration Center by launching Team Foundation Server Administration Console.
Required Permissions
You must be a member of the Administrators security group on the server on which you will configure TFS.
To configure Team Foundation Server to accept Kerberos Tickets:
-
In the Team Foundation Server Administration Console, select the Application Tier settings.
-
On the Application Tier settings, select Authentication Settings.
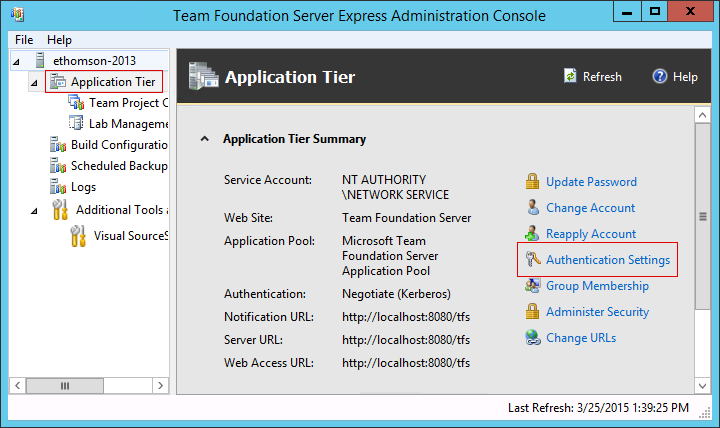
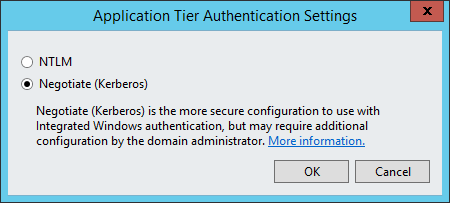
-
In the Authentication Settings dialog box, select Kerberos. This will enable both Kerberos and NTLM authentication.
A service principal name links the Active Directory service account running your Team Foundation Server instance to the service itself, and is required for Kerberos authentication to your Team Foundation Server.
Required Permissions
You must be a member of the Domain Administrators or Enterprise Administrators security group, or have been delegated the Validated Write to Service Principal Name permission, on the server on which you will configure an SPN.
You should configure an SPN for the fully-qualified domain name as well
as the short name of the machine. If your server name is
servername.contoso.com, you should configure an SPN for HTTP/servername
and HTTP/servername.contoso.com.
If your Team Foundation Server Application Tiers are configured to use a network service account then you must configure an SPN for the computer account. For example:
setspn -c -S HTTP/servername SERVERNAME$ setspn -c -S HTTP/servername.contoso.com SERVERNAME$
If your Team Foundation Server Application Tiers are configured to use
a domain account then you must configure an SPN for the domain account
instead. If the application tiers are configured to run as
CONTOSO\tfsuser for example:
setspn -c -S HTTP/servername CONTOSO\tfsuser setspn -c -S HTTP/servername.mycompany.com CONTOSO\tfsuser
For more information, see the [https://technet.microsoft.com/en-us/library/cc731241(WS.10).aspx](setspn documentation) on Microsoft TechNet.
Ensure that you have a Kerberos Ticket Granting Ticket (TGT) for your
user principal. If you log in to the computer using your Kerberos
credentials, this may be done for you. If not, you may perform this
manually using the kinit command and providing your Active Directory
domain credentials, specifying the Active Directory domain as its DNS name.
For example, the user CONTOSO\testuser should be specified as
testuser@CONTOSO.COM:
kinit testuser@CONTOSO.COM
You can verify that you have a TGT using the klist command. You should
see a “default principal” specified as testuser@CONTOSO.COM.
Finally, you may use the git tool with a Team Foundation Server remote repository. To indicate to git that it should authenticate with your Kerberos credentials, enter an empty username and password. For example, to clone a repository named “Test”:
git clone http://servername.contoso.com:8080/tfs/DefaultCollection/Test
And simply press Enter when prompted for your username and password.
-
Ensure that your Team Foundation Server accepts Kerberos credentials. Use a network monitoring tool such as Wireshark or Fiddler to examine a successful connection from Visual Studio to Team Foundation Server. If the connection uses NTLM authentication instead of Kerberos, examine your server configuration.
-
Ensure that your git client was compiled with the Kerberos system libraries. Use a network monitoring tool to examine an unsuccessful connection from git to TFS. If the connection does not attempt to use Kerberos, contact your operating system vendor for assistance.